How Quantum Computing is Revolutionizing Data Security
Understanding Quantum Computing and Its Potential
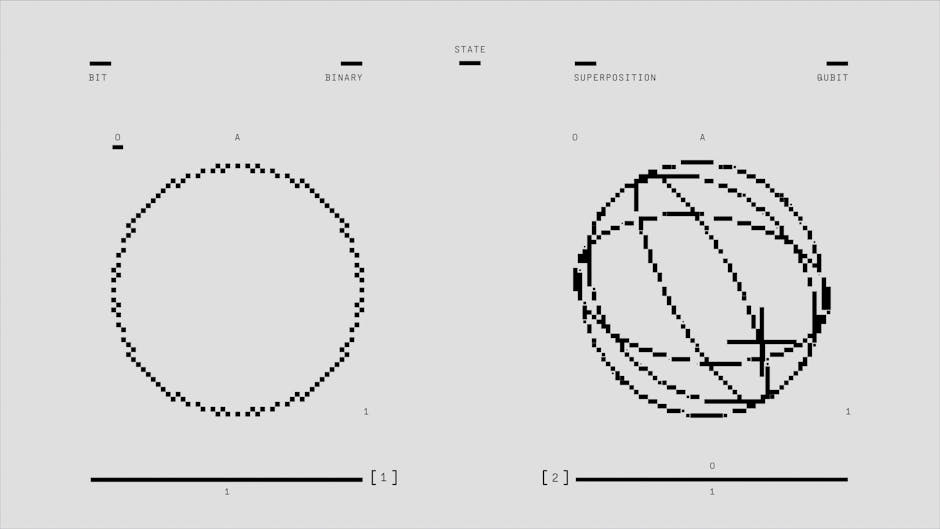
Quantum computing is a groundbreaking technology that leverages principles of quantum mechanics to perform complex computations at unprecedented speeds. Unlike traditional computers, which use bits as the smallest unit of data, quantum computers use qubits, enabling them to process multiple possibilities simultaneously.
The Impact on Data Security
One of the most significant areas affected by quantum computing is data security. Traditional encryption methods, such as RSA and ECC, rely on the difficulty of factoring large numbers or solving discrete logarithms, which quantum algorithms like Shor's algorithm can potentially solve efficiently, rendering current cryptographic systems vulnerable.
Quantum Cryptography and Secure Communication
To counteract these threats, researchers are developing new techniques like quantum cryptography, which uses the principles of quantum mechanics to create secure communication channels. Protocols such as Quantum Key Distribution (QKD) enable two parties to share encryption keys with guaranteed security since any eavesdropping attempts disturb the quantum states, alerting the users to potential breaches.
Future of Cybersecurity
As quantum technology continues to advance, cybersecurity measures will need to evolve to remain effective. Organizations are investing in post-quantum cryptography algorithms designed to withstand quantum attacks, ensuring data remains protected in a quantum-enabled world.
Conclusion
Quantum computing has the potential to revolutionize data security by both exposing vulnerabilities in current cryptographic systems and offering innovative solutions like quantum cryptography. Preparing for this new era is crucial for safeguarding information and maintaining privacy in the future.

